Wired Equivalent Privacy — Wikipédia
A wikipedia article, free l’encyclopéi.
For homonymous articles, see Wired.
The Wired Equivalent Privacy (abridged WEP ) is a protocol to secure wireless wireless networks. Wireless networks diffusing messages exchanged by radio waves are particularly sensitive to clandestine listening. WEP takes its name from the fact that it had to provide wireless networks with confidentiality comparable to that of a classic local wired network.
However, several serious weaknesses have been identified by cryptologists. WEP is sometimes nicknamed with the nickname of Weak Encryption Protocol . The WEP was therefore supplanted by WPA in 2003, then by WPA2 in 2004 (WPA2 is the version of the IEEE 802.11i standard certified by Wi-Fi Alliance) [ first ] .
Despite its intrinsic weaknesses, the WEP provided for a time a minimum level of security which could discourage the least experienced attackers. Today if WEP network cracking utilities like Aircrack-Ng under GNU/Linux still require some knowledge, the most novice attackers can have since Commercial boxes at less than 150 € that operate without human intervention, automatically look for WEP connections 1 km around, decorate them and thus provide a free internet connection to any computer linked to it, regardless of the operating system. All as anonymously as an anonymous as it.
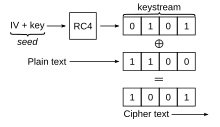
The WEP is part of the IEEE 802.11 standard ratified in September 1999. WEP uses the RC4 flowing algorithm to ensure confidentiality and the CRC-32 control sum to ensure integrity.
The 64 -bit WEP uses a 40 -bit encryption key to which an initialization vector ( initialization vector or IV in English) of 24 bits. The key and the initialization vector thus form a 64 -bit RC4 key to quantify the data exchanged. As the WEP standard has been written, the restrictions imposed by the United States government of America on the export of cryptographic means limited the size of the keys. Once these restrictions have been removed, the main manufacturers extended the WEP to 128 -bit using a 104 -bit key.
A 128 -bit WEP key is entered as a series of 13 ASCII characters or 26 hexadecimal characters. Each double hexadecimal represents 8 bits of the WEP key. 8 * 13 = 104 bits. By adding the 24 -bit initialization vector (IV), you get what is called “a 128 -bit WEP key”.
A mechanism using 256 -bit WEP keys is available. As with the mechanisms previously mentioned, 24 bits are reserved for the initialization vector (IV), thus leaving 232 bits for the encryption key. This key is usually seized as a series of 58 hexadecimal symbols. (58 * 4 = 232 bits) + 24 = 256 bits.
Unfortunately, the length of the keys is not the most severe security problem in WEP.
Because RC4 is a flow encryption algorithm, the same key should not be used twice to quantify the data exchanged. This is the reason for the presence of an initialization vector (IV). This vector, transmitted without protection, makes it possible to avoid repetition. However, a 24 -bit IV is not long enough to avoid this phenomenon on a very active network. In addition, the initialization vector is used in such a way that it makes WEP sensitive to a related key attack.
Many WEP systems require that the key will be entered in hexadecimal. Some users choose keys that form words with symbols 0 to 9 and A to F ( 1234 5678 dead beef For example). Such keys can most often be easily guessed.
In August 2001, Fluhrer et al. has published a cryptological analysis which exploits the way that RC4 and IV algorithm are used in WEP. This analysis reveals a passive attack that allows you to find the RC4 key after illegal listening to the network for a few hours. The attack was quickly implemented and automated tools have been published since then. It is possible to make this type of attack with a personal computer, current hardware and software available free of charge.
Cam-Winget et al. (2003) studied a series of imperfections in WEP. They write : ” Experiments in the field indicate that, with proper equipment, it is practical to eavesdrop on WEP-protected networks from distances of a mile or more from the target “(Which means in French:” Experiments in this area indicate that with adequate equipment it is easy to spy on networks protected by WEP at a distance from a mile or more »). In addition, they report two general weaknesses:
- WEP is optional, many facilities have never activated it;
- WEP does not include a key management protocol, the mechanism resting instead on a single key shared between all users.
In 2005, an FBI team from the United States of America demonstrated that it is possible to penetrate a network protected by WEP in 3 minutes using publicly available tools (for example thanks to Aircrack-Nvary software available under Linux and Windows).
Since July 2006, it is possible to penetrate the networks protected by WEP in just a few seconds, by taking advantage of the fragmentation of the packages to accelerate the breaking of the key. The details of this technique are explained in the article in English “A final nail in WEP’s Coffin” ( A last nail in the WEP coffin )
To compensate for WEP security problems, it is very widely recommended to replace WEP (as well as WPA) with WPA2 [ 2 ] . Both provide much better security. Some old Wi-Fi access points may need to be replaced to allow the transition to one or the other mechanism. However, these replacements are relatively inexpensive. The implementation of tunnels, like IPSEC tunnels, is an alternative to WEP. If WEP must ever be kept for one reason or another, it is recommended to set up a VPN.
Recent Comments