Zygalski leaves – Wikipedia
A wikipedia article, free l’encyclopéi.
The method of Zygalski leaves is a cryptological technique used by the Biuro Szyfrów Polish, before and during the Second World War, then by British cryptologists from Bletchley Park, in order to decipher encrypted messages using the German system of Enigma.
Zygalski’s leaves took the name of their inventor of , Henryk Zygalski.
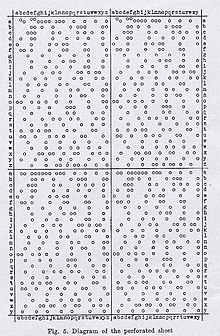
The Zygalski device includes a game of 26 perforated sheets for each of the six possible initial sequences of inserting the three rotors in the jammer of the Enigma machine [ first ] . Each sheet is related to the starting position of the left rotor, the one that moves the most slowly.
The 26×26 matrix, which represents the 676 possible starting positions for the left and midfielder, was duplicated horizontally and vertically: a– With , a– and . The leaves were pierced with holes in the positions that would allow the occurrence of a “female”.
Marian Rédwski explains the implementation of the apparatus with perforated sheets: “When the leaves are superimposed and moved, in relation to each other, in good sequence and in the right way, depending on a strictly defined program, The number of visible openings gradually decreases. And, if a sufficient amount of data is available, there is ultimately only one opening, which probably corresponds to the right case, that is to say the solution. From the position of the opening, we can calculate the order of the rotors, the arrangement of their rings, and, by comparison of the letters of the indicator and the letters of the machine, also the permutation s; In other words, the whole key of encryption. »» [ 2 ]
Like the Carte Catalog method that Réjwski had developed by means of its cyclometer, the procedure for Zygalski sheets is independent of the number of plugs in the connection table [ 3 ] .

Manufacturing takes too long. For security reasons, the leaves are perforated by the mathematicians themselves [ 4 ] , by means of razor blades. THE , only a third of the task is finished.
On this date, the Germans introduce Rotors IV and V, multiplying by ten the quantity of work, since it would have taken ten times more sheets (for the 60 combinations of possible sequences of the three rotors selected from five) [ 3 ] .
The , five weeks before the invasion of Poland, in Warsaw, the Polish figure office reveals to its French and British guests its successes in the decryption of Enigma [ 5 ] . Certain revelations concern the method of perforated sheets of Zygalski.
In Bletchley Park, the British undertake the production of two complete games of perforated leaves. The work is performed, by means of perforators, by a section led by John R.F. Jeffreys [ 6 ] , [ 7 ] . At BP, these leaves are baptized network (of Network proceedings , “net method”), although in the memory of Gordon Welchman these are the “Jeffreys leaves”; Although these Jeffreys sheets are rather those of another catalog produced by the Jeffreys section [ 6 ] .
The first game is finished at the end . The , part of the second game is delivered to Polish cryptologists refugees to PC Bruno [ 7 ] . Finished on , the remaining leaves are brought by Turing shortly after [ 7 ] . “With these sheets, writes Rejewski, we continued to resolve the daily keys.” [ 3 ] The leaves allow Poles to decipher their first Enigma message from wartime, the [ 7 ] , [ 8 ] .
In , the Germans, once again, completely modify their method of encryption of the key (except for their Norwegian network). As a result, Zygalski’s leaves are no longer useful. The relay is taken by the truc by John Herivel (Herivel Tip) [ 9 ] .
- On December 15, 1938, the Germans went from three to five rotors. Only three are put into service both in the machine, but the number of possible arrangements jumps from 6 to 60. Result, it would take 60 games of perforated sheets. Marian Réjwski, “Summary of Our Methods for Reconstructure Enigma and Recontructure Daily Keys …”, Appendix C to Władysław Kozaczuk, Enigma , 1984, p. 242–43 .
- Marian Rejewski, “The Mathematical Solution of the Enigma Cipher,” Appendix E to Władysław Kozaczuk, Enigma , 1984, p. 289 .
- Marian Rejewski, “Summary of Our Methods for Reconstructing ENIGMA and Reconstructing Daily Keys…”, Appendix C to Władysław Kozaczuk, Enigma , 1984, p. 243 .
- Marian Rejewski, “Remarks on Appendix 1 to British Intelligence in the Second World War by F.H. Hinsley,” p. 82 .
- Władysław Kozaczuk, Enigma , 1984, p. 59 .
- Ralph Erskine, “The Poles Reveal their Secrets: Alastair Denniston’s Account of the July 1939 Meeting at Pyry,” Cryptologia 30 (4), December 2006, p. 294–305 .
- Ralph Erskine, “Breaking Air Force and Army Enigma,” in Action this Day , edited by Ralph Erskine and Michael Smith, 2001, p. 53 .
- Władysław Kozaczuk, Enigma , 1984, p. 84 , 94 (note 8).
- Marian Rejewski, “Summary of Our Methods for Reconstructing ENIGMA and Reconstructing Daily Keys…”, Appendix C to Władysław Kozaczuk, Enigma , 1984, p. 243 , 245.
Recent Comments